tl;dr: Don t just
apt install rustc cargo. Either do that and make sure to use only Rust libraries from your distro (with the tiresome config runes below); or, just use
rustup.
Don t do the obvious thing; it s never what you want
Debian ships a Rust compiler, and a large number of Rust libraries.
But if you just do things the obvious default way, with
apt install rustc cargo, you will end up using Debian s
compiler but
upstream libraries, directly and uncurated from crates.io.
This is not what you want. There are about two reasonable things to do, depending on your preferences.
Q. Download and run whatever code from the internet?
The key question is this:
Are you comfortable downloading code, directly from hundreds of upstream Rust package maintainers, and running it ?
That s what
cargo does. It s one of the main things it s
for. Debian s
cargo behaves, in this respect, just like upstream s. Let me say that again:
Debian s cargo promiscuously downloads code from crates.io just like upstream cargo.
So if you use Debian s cargo in the most obvious way, you are
still downloading and running all those random libraries. The only thing you re
avoiding downloading is the Rust compiler itself, which is precisely the part that is most carefully maintained, and of least concern.
Debian s cargo can even download from crates.io when you re building official Debian source packages written in Rust: if you run
dpkg-buildpackage, the downloading is suppressed; but a plain
cargo build will try to obtain and use dependencies from the upstream ecosystem. ( Happily , if you do this, it s quite likely to bail out early due to version mismatches, before actually downloading anything.)
Option 1: WTF, no I don t want curl bash
OK, but then you must limit yourself to libraries available
within Debian. Each Debian release provides a curated set. It may or may not be sufficient for your needs. Many capable programs can be written using the packages in Debian.
But any
upstream Rust project that you encounter is likely to be a pain to get working, unless their maintainers specifically intend to support this. (This is fairly rare, and the Rust tooling doesn t make it easy.)
To go with this plan,
apt install rustc cargo and put this in your configuration, in
$HOME/.cargo/config.toml:
[source.debian-packages]
directory = "/usr/share/cargo/registry"
[source.crates-io]
replace-with = "debian-packages"
This causes cargo to look in
/usr/share for dependencies, rather than downloading them from crates.io. You must then install the
librust-FOO-dev packages for each of your dependencies, with
apt.
This will allow you to write your own program in Rust, and build it using
cargo build.
Option 2: Biting the curl bash bullet
If you want to build software that isn t specifically targeted at Debian s Rust you will probably
need to use packages from crates.io,
not from Debian.
If you re doing to do that, there is little point not using
rustup to get the latest compiler. rustup s install rune is alarming, but cargo will be doing exactly the same kind of thing, only worse (because it trusts many more people) and more hidden.
So in this case:
do run the
curl bash install rune.
Hopefully the Rust project you are trying to build have shipped a
Cargo.lock; that contains hashes of all the dependencies that
they last used and tested. If you run
cargo build --locked, cargo will
only use those versions, which are hopefully OK.
And you can run
cargo audit to see if there are any reported vulnerabilities or problems. But you ll have to bootstrap this with
cargo install --locked cargo-audit; cargo-audit is from the
RUSTSEC folks who do care about these kind of things, so hopefully running their code (and their dependencies) is fine. Note the
--locked which is needed because
cargo s default behaviour is wrong.
Privilege separation
This approach is rather alarming. For my personal use, I wrote a privsep tool which allows me to run all this upstream Rust code as a separate user.
That tool is
nailing-cargo. It s not particularly well productised, or tested, but it does work for at least one person besides me. You may wish to try it out, or consider alternative arrangements.
Bug reports and patches welcome.
OMG what a mess
Indeed. There are large number of technical and social factors at play.
cargo itself is deeply troubling, both in principle, and in detail. I often find myself severely disappointed with its maintainers decisions. In mitigation, much of the wider Rust upstream community
does takes this kind of thing very seriously, and often makes good choices.
RUSTSEC is one of the results.
Debian s technical arrangements for Rust packaging are quite dysfunctional, too: IMO the scheme is based on fundamentally wrong design principles. But, the Debian Rust packaging team is dynamic, constantly working the update treadmills; and the team is generally welcoming and helpful.
Sadly last time I explored the possibility, the Debian Rust Team didn t have the appetite for more fundamental changes to the
workflow (including, for example,
changes to dependency version handling). Significant improvements to upstream cargo s approach seem unlikely, too; we can only hope that eventually someone might manage to supplant it.
edited 2024-03-21 21:49 to add a cut tag
comments
 Turns out that VPS provider Vultr's
Turns out that VPS provider Vultr's

 Thanks to All Saints Day, I ve just had a 5 days weekend. One of those
days I woke up and decided I absolutely needed a cartonnage box for the
cardboard and linocut
Thanks to All Saints Day, I ve just had a 5 days weekend. One of those
days I woke up and decided I absolutely needed a cartonnage box for the
cardboard and linocut  One of the boxes was temporarily used for the plastic piecepack I got
with the
One of the boxes was temporarily used for the plastic piecepack I got
with the 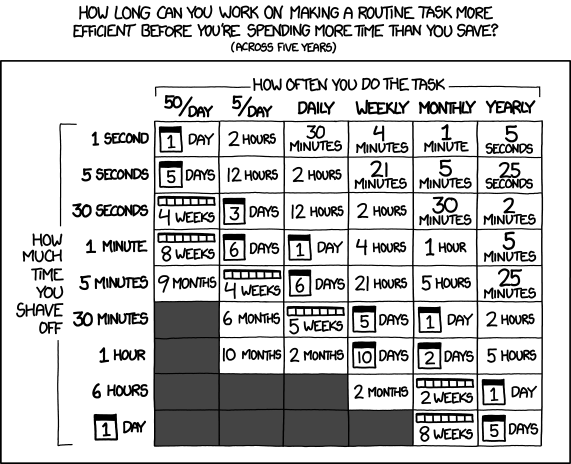 One of the most common fallacies programmers fall into is that we will jump
to automating a solution before we stop and figure out how much time it would even save.
In taking a slow improvement route to solve this problem for myself,
I ve managed not to invest too much time
One of the most common fallacies programmers fall into is that we will jump
to automating a solution before we stop and figure out how much time it would even save.
In taking a slow improvement route to solve this problem for myself,
I ve managed not to invest too much time This article is cross-posting from grow-your-ideas. This is just an idea.
This article is cross-posting from grow-your-ideas. This is just an idea.

 A first revision of the still only one-week old (at
A first revision of the still only one-week old (at 
 Like each month, have a look at the work funded by
Like each month, have a look at the work funded by  The image here comes from an example of building
The image here comes from an example of building  I like using one machine and setup for everything, from serious development work to hobby projects to managing my finances. This is very convenient, as often the lines between these are blurred. But it is also scary if I think of the large number of people who I have to trust to not want to extract all my personal data. Whenever I run a
I like using one machine and setup for everything, from serious development work to hobby projects to managing my finances. This is very convenient, as often the lines between these are blurred. But it is also scary if I think of the large number of people who I have to trust to not want to extract all my personal data. Whenever I run a 












 The key idea of
The key idea of 
 The talks held in the room were these below, and in each of them you can watch the recording video.
The talks held in the room were these below, and in each of them you can watch the recording video.




 As there has been an increase in the number of proposals received, I believe that interest in the translations devroom is growing. So I intend to send the devroom proposal to FOSDEM 2025, and if it is accepted, wait for the future Debian Leader to approve helping me with the flight tickets again. We ll see.
As there has been an increase in the number of proposals received, I believe that interest in the translations devroom is growing. So I intend to send the devroom proposal to FOSDEM 2025, and if it is accepted, wait for the future Debian Leader to approve helping me with the flight tickets again. We ll see.